This advice was originally proposed by Peter Nazarov (Twitter, LinkedIn), who kindly asked me to give it a bigger spread.
The biggest question for the day is if the fix was already applied to all official Sitecore container images so that now we can just pull new Sitecore containers and rebuild to rebuild our own container images to apply the patch?
The KB article offers WDP and ZIP packages fixes but says noting about containers, just like containers are not supported by Sitecore:
Critical vulnerability applicable to all Sitecore versions related to XSS.
This issue is related to a Cross Site Scripting (XSS) vulnerability which might allow authenticated Sitecore users to execute custom JS code within Sitecore Experience Platform (XP) and Sitecore Managed Cloud.
We encourage Sitecore customers and partners to familiarize themselves with the information below and apply the Solution to all affected Sitecore instances. We also recommend that customers maintain their environments in security-supported versions and apply all available security fixes without delay.
So below are some findings:
So to apply the fix for your Docker images you need to copy the patch files from the following Sitecore Docker assets images:
- for XM1:
scr.sitecore.com/sxp-pre/sitecore-xm1-assets:10.2.1.007064.169-10.0.17763.2366-1809
- for XP0:
scr.sitecore.com/sxp-pre/sitecore-xp0-assets:10.2.1.007064.169-10.0.17763.2366-1809
- for XP1:
scr.sitecore.com/sxp-pre/sitecore-xp1-assets:10.2.1.007064.169-10.0.17763.2366-1809
For example, if using XM1: scr.sitecore.com/sxp-pre/sitecore-xm1-assets:10.2.1.007064.169-10.0.17763.2366-1809 for XM 10.2.0.
Inside this Sitecore Docker assets image you find C:\platform\ directory which contains the directories for the corresponding Docker images that you need to patch:
- \platform\cd
- \platform\cm
- \platform\id (it is empty and can be ignored)
You will need to copy the content of those directories to file system root C:\ of the corresponding container.
For your \docker\build\cm\Dockerfile you would need a couple of new lines:
...
FROM scr.sitecore.com/sxp-pre/sitecore-xm1-assets:10.2.1.007064.169-10.0.17763.2366-1809 as kb1001489
...
FROM ${BASE_IMAGE}
...
WORKDIR C:\
COPY --from=kb1001489 /platform/cm/ ./
You would need to do similar changes to your \docker\build\cd\Dockerfile with only one difference that you copy the CD patch files instead of CM in the last line:
...
COPY --from=kb1001489 /platform/cd/ ./
Of course, you can introduce the .env variable for scr.sitecore.com/sxp-pre/sitecore-xm1-assets:10.2.1.007064.169-10.0.17763.2366-1809 and pass it to your docker files as an ARG.
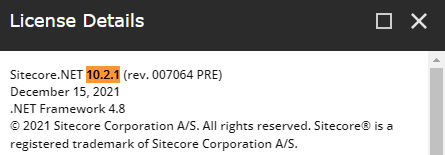
Note: this patch changes the version of your Sitecore 10.2.0 instance to 10.2.1: Sitecore.NET 10.2.1 (rev. 007064 PRE) (see the screenshot below). Seeing this happening it feels that, sadly, Sitecore is unlikely to release 10.2.0 Docker that includes this patch - it would cause versioning issues:
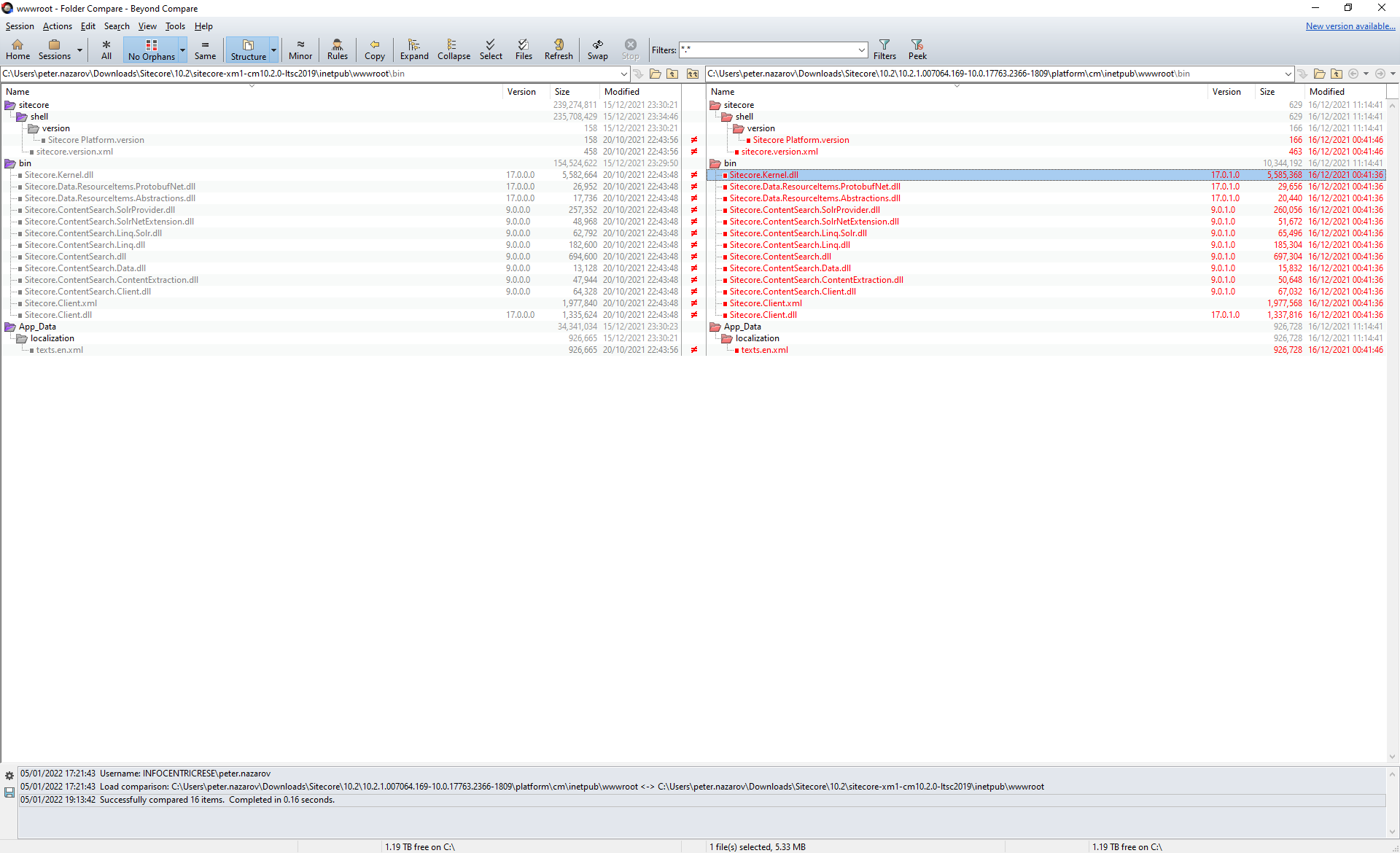
The example above is good to learn how you apply a patch with Docker assets image-based patch to your containers.
However, this Cumulative fix for Sitecore XP 10.2 patch changes a lot of DLLs to the new version which are not exposed via NuGet feed, and changes your Sitecore version to a pre-release version (which does not exist). This would give you several challenges. Therefore, I would prefer in this specific case to apply just a standard .zip file-based fix as per Notes section on the page:
For Sitecore XP 10.1 and later, if it is not possible to apply the cumulative fix (pre-release update), the following patch can be applied alternatively: Sitecore.Support.500712.zip.
- Changes multiple DLL versions (they are not available in NuGet feed)
- Changes Sitecore version to a pre-release version (next version that is not released yet)
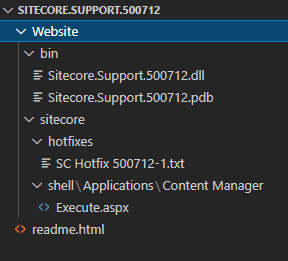
Sitecore.Support.500712.zip
- Deploys new
Sitecore.Support.500712.dll
- Overwrites vulnerable
\sitecore\shell\Applications\Content Manager\Execute.aspx page file so that it runs from Sitecore.Support.500712.dll which contains the fix.